User authentication / Identity provider
Select and configure the identity manager you use for user authentication.
Active Directory
| Option | Example | Description | |
|---|---|---|---|
| (A)1 | Server | ldaps://dc.int.sampletec-01.com:636 | LDAP protocol and FQDN, or the IP address of the AD server (Domain Controller) For LDAPS, you need a Base64-encoded CA certificate, see below. |
| Base | DC=int,DC=sampletec-01,DC=com | LDAP search base of the Active Directory domain | |
| Group template | SCG_Group_ | Prefix used for the newly created AD groups The prefix is used to authenticate users and assign devices to OUs of the Scout Server. Only users who are members of an AD group with this configured prefix can log on to the Scout Cloud Gateway. |
|
| CA certificates | Base64-encoded CA certificate (.pem for secure LDAPS communication (LDAP over SSL) To convert from .der to .pem, use openssl: |
-
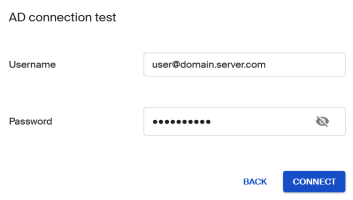
To check whether you can connect to the AD service with the specified AD data (without a new route), click Test connection.
Enter the username and password of a test user and click Connect.
Note:
The username must be specified as a user principal name (UPN).
Example: mmi@int.sampetec-01.com
OpenID Connect / Keycloak
View the configuration data for your Keycloak client in the Keycloak administration console under Installation > Format Option: Keycloak OIDC JSON
For further information on configuring Keycloak, see Configuring Keycloak.
| Option | Example | Description | |
|---|---|---|---|
| Keycloak realm | ScoutEnterpriseCloudGateway | Name of the realm you have created in the Keycloak administration console for your environment | |
| Keycloak server auth URL | https://keycloak.int.sampletec-01.com:8443/auth | Server authentication URL as specified in your Keycloak client on the Installation tab Note: For authentication via Keycloak, only HTTPS is supported. For this you need a CA certificate. |
|
| Keycloak client ID | SCG | Name of your Keycloak client you have specified in Keycloak under Settings > Client ID | |
| Keycloak client secret | u14n936i-2642-43fc-o911-8n5de21a0e76 | Key generated by Keycloak for your Client ID, in Keycloak under Credentials > Secret |
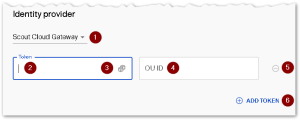
Scout Cloud Gateway authentication
The Scout Cloud Gateway supports a token-based logon for the registration of new devices. You may create as many tokens as you like and give them to users to register their device.
You can have a token created automatically or create it manually.
-
To create a new token, click Add token. Assign an OU to the token.
| 1 | Select Identity provider Scout Cloud Gateway. |
| 2 | Enter a new token (option A) A token must have a minimum of 16 and a maximum of 50 characters. Allowed characters:
|
| 3 | Generate a new token (option B)2 |
| 4 | ID for the OU in which the user's device is to be registered during on-boarding |
| 5 | Delete token / entry |
| 6 | Create a new entry |
User/password authentication
Up to eLux RP 6.10, the definition of SCG users with password was provided. For compatibility reasons, this method is still supported.
-
Select Support user/password authentication and add new user entries.