Configuring Keycloak
Keycloak is an open source solution for identity and access management and is based on the OpenID Connect protocol. In order to use Keycloak for user logon, Keycloak must be configured on the server side and a Keycloak client must be installed.
All users whose devices are to be connected to their Scout Server via the Scout Cloud Gateway must be authorized via Keycloak roles.
-
Set up a Keycloak server.
To protect sensitive data, only HTTPS configuration is supported. For this you need a CA certificate.
-
In the Keycloak administration console, create a realm for your environment.
-
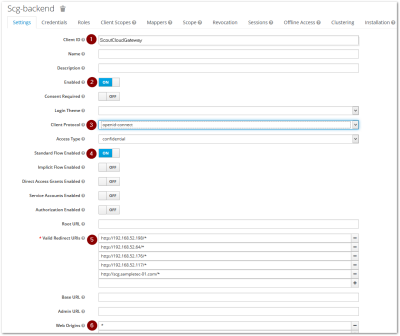
Create a Keycloak client for your application. For the Keycloak client, edit any options labeled on the figure below.
Option Description Settings > Client ID Name of your client / application Settings > Valid Redirect URIs One or more SCG addresses to which Keycloak forwards users after successful authentication -
Within your client, create roles and users. Assign a role to each user.
Users are authorized to access their Scout Server via the Scout Cloud Gateway and can register their devices once the gateway is configured. The devices are assigned to the default OU defined in the Scout Console.