Scout Cloud Gateway in a DMZ
For the setup of the Scout Cloud Gateway in your network, we recommend the operation in a security-controlled 'Demilitarized Zone',
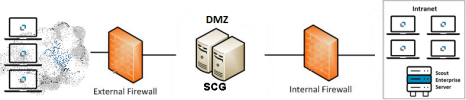
The following routes must be set up for configuration:
-
From the eLux devices to the DMZ
You define these routes in the SCG WebAdmin interface under Configuration > VPN device settings > Routes.
-
From the Scout Cloud Gateway to the Intranet
For further information, see Static IP routes.
-
From the Scout Server, AD server / identity manager and other required (application) servers back to the Scout Cloud Gateway in the DMZ
For further information, see General network settings.
Use dedicated firewall rules to control access from the Internet to the DMZ and from the DMZ to the Intranet.
To use the Scout Cloud Gateway as a router between DMZ and Intranet, you can use a second network card. In the VM installation, two network cards are already considered and can be configured.
Note the following
-
If you intend to use multiple SCG instances in a cluster, they must also be able to communicate with each other.
-
If you define a gateway and DNS only for the internal network, make sure that the names of the Scout Server and AD server / identity manager can be resolved.
Example for configuring routes
Premises:
(A) eLux devices are supposed to access resources on the Intranet (network 192.168.50.0/24).
(B) The SCG is located in a DMZ with network 192.168.100.0/24 and connects eLux devices via tunnel network 10.8.0.0/24.
(C) Both networks are connected via a router/gateway, with address 192.168.100.1 in the DMZ and 192.168.50.1 in the Intranet.
Required routes:
A) Network: 192.168.50.0, subnet mask: 255.255.255.0 (gateway is the VPN server of the SCG)
B) Network: 192.168.50.0, subnet mask: 255.255.255.0, gateway from DMZ to intranet: 192.168.100.1
C) Network: 10.8.0.0, subnet mask: 255.255.255.0, gateway from the intranet into the DMZ: 192.168.50.1
For further information, see General configuration.